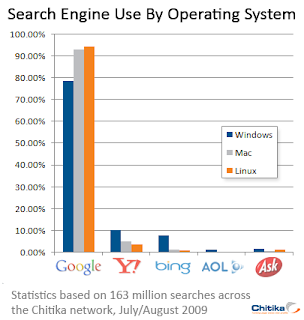
Reference:
_______________________________________________________
Seven things Windows 7 can learn from Linux
I’m so excited about the release of Windows 7. Yes, really, an old Linux tragic like me can’t wait for Microsoft’s next-generation OS. But that doesn’t mean Microsoft should stop learning. Far from it, let’s consider the perfect number of moves Redmond can make to take a leaf out of Linux’s book – for the benefit of all.
The number 7 has held a special place in numerology and mythology for centuries. Wikipedia even has page explaining its significance at: http://en.wikipedia.org/wiki/7_(number).
When Windows 7 hits the scene on October millions of people will be immersed in the word 7 for the foreseeable future. How do you make something perfect even better? You learn from your competitors.
So without dwelling on the number, here are seven ways Windows 7 can improve by adopting concepts from Linux.
1. More frequent release cycles. As I’ve already explained, Microsoft’s worst enemy has been its very long release cycles. Linux distributors, on the other hand, have the opposite problem – too frequent release cycles. But what would a consumer be more interested in, an operating system that’s eight years old (Windows XP) or one that’s updated every year or even six months? Fresh product releases means fresh marketing and Microsoft knows this. From Windows 7 on it’s bye, bye many-year release cycles and hello two year cycles at the most.
2. Sane release versioning. Okay, before anyone comments about how INSANE Linux distribution release versioning is, it’s still not as bad as Windows’. Yes, there is a systematic way in which Microsoft versions its Windows releases, but that’s been hidden behind the marketing hoopla. We’ve had Windows 3.1, 95, NT, 98, 2000, Me, XP, Vista and 7 which makes perfect sense. Suddenly Ubuntu’s 7.10, 8.04, 8.10, 9.04, etc, doesn’t seem so silly after all. Nor does Fedora’s 8, 9, 10. Mac OS X? This stays the same with just minor release versions and code names - brilliant for the not-so-tech-savvy. Dumb it down Microsoft. If you’re going to name a product Windows 7, release Windows 8 after it, not “Windows Panorama” or “Windows 2012”.
3. Online OS upgrades. One thing Linux does well is allow users to perform a major OS release upgrade online. Microsoft’s boxed set cash cow may prevent this from happening soon, but it’s something that definitely should be on its radar. Want to upgrade to the next version? Click a box, pay for it and download it over the Internet. The same can be said about third-party applications as well.
4. Better Web app integration. If Microsoft learns anything from Linux or Mac OS X is that today’s desktop user is obsessed with Web apps and will do anything to get Facebook and Twitter functionality at their fingertips. The KDE hackers wrote an entire widget development framework for transferring data over the Internet and it’s now available with every modern Linux distribution. While I have no doubt Windows 7 will have enough clout to force developers into writing Web 2.0 widgets. The big questions are how much traction it will get and how long will it take. Will the native Windows 7 widgets capture people’s interest the way the others have? Microsoft needs to make it happen.
5. Support open development environments. Microsoft has come a long way with its support for standards-based development environments since the ugly tiff with Java a few years back. I’d love to see Windows 7 and its predecessors take this one step further. If it’s and open source, standards-based development environment then it can be used on Linux and this is holding Windows back. Microsoft needs to leave the politics of programming environment source code behind and give developers the tools they need, right there in the operating system. Develop bindings for open source languages and let ISVs create commercial applications. Get the great development projects on Codeplex into the OS proper.
6. Slim down for the mobile world. The rise of Linux netbooks and smartphones over the past 12 months has surely given Microsoft incentive to slim down future versions Windows. If not slim down Windows entirely, at the very least break the shackles of a monolithic product and componentise it so the OEMs can ship just what they need for their mobile computer. Sure there’s Windows Mobile, but like Symbian it was not designed to work on a small notebook. Linux is attractive to netbook markers because it can be cut down and customized for smaller, lighter end of the market. And with Windows Vista being the resource hog that it was, Windows 7 has a big task ahead to match the nimble Linux.
7. Better device support. One of the greatest misconceptions about Linux is that there is limited, if any, support for internal and external devices. In fact, the Linux kernel ships with more device drivers than any other operating system. If a device is support there is a good chance it will work with Linux. Windows, however, still relies heavily on its expansive network OEMs and ISVs to provide the functionality people expect when they purchase an after market product. Windows 7 needs to be the release that aggressively begins to integrate device drivers into the operating system they was Linux and Mac OS X have. This also helps people that are not chained to the same computer or location getting stuck without driver CDs.
So there are seven things Windows 7 can learn from Linux to make the world a better place. Feel free to suggest seven more, or, even better, take them up with Microsoft once lucky 7 shines upon us later this year.